Introduction to Fraud Detection
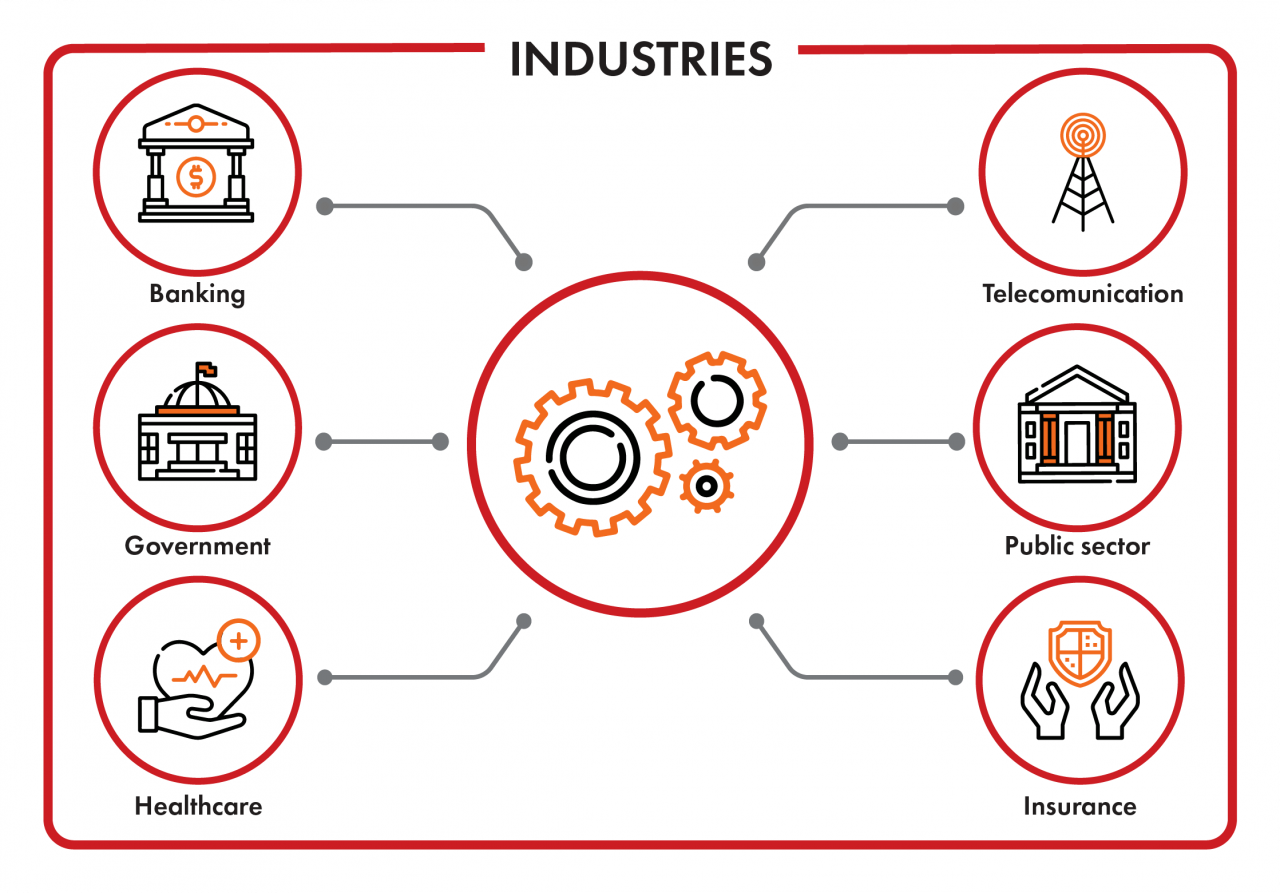
Fraud today is a billion dollar business conducted in almost every industry but mostly in banking, insurance, healthcare, telecommunications and public sector. Fraud has a few definitions but in essence it covers wrongful and criminal activities intended to result in financial or personal gain like embezzling, theft and scams. Fraud can be committed by people within or outside the organization.
Up until recently businesses were safe by running their fraud detection processes once a day, usually at the end of the working day. But now we can be sure that those traditional fraud detection systems are no longer up to the task. As today we have an increased number of devices to perform the transactions like laptops, computers, mobile phones, tablets and other personal devices fraudulent activities are much more complex and sophisticated as they are performed through various channels. So as the fraudulent activities become progressively complicated the businesses today abandon the struggle with the traditional fraud detection systems and turn to superior, real time fraud detection.
Fraud Detection Is a Dynamic Process
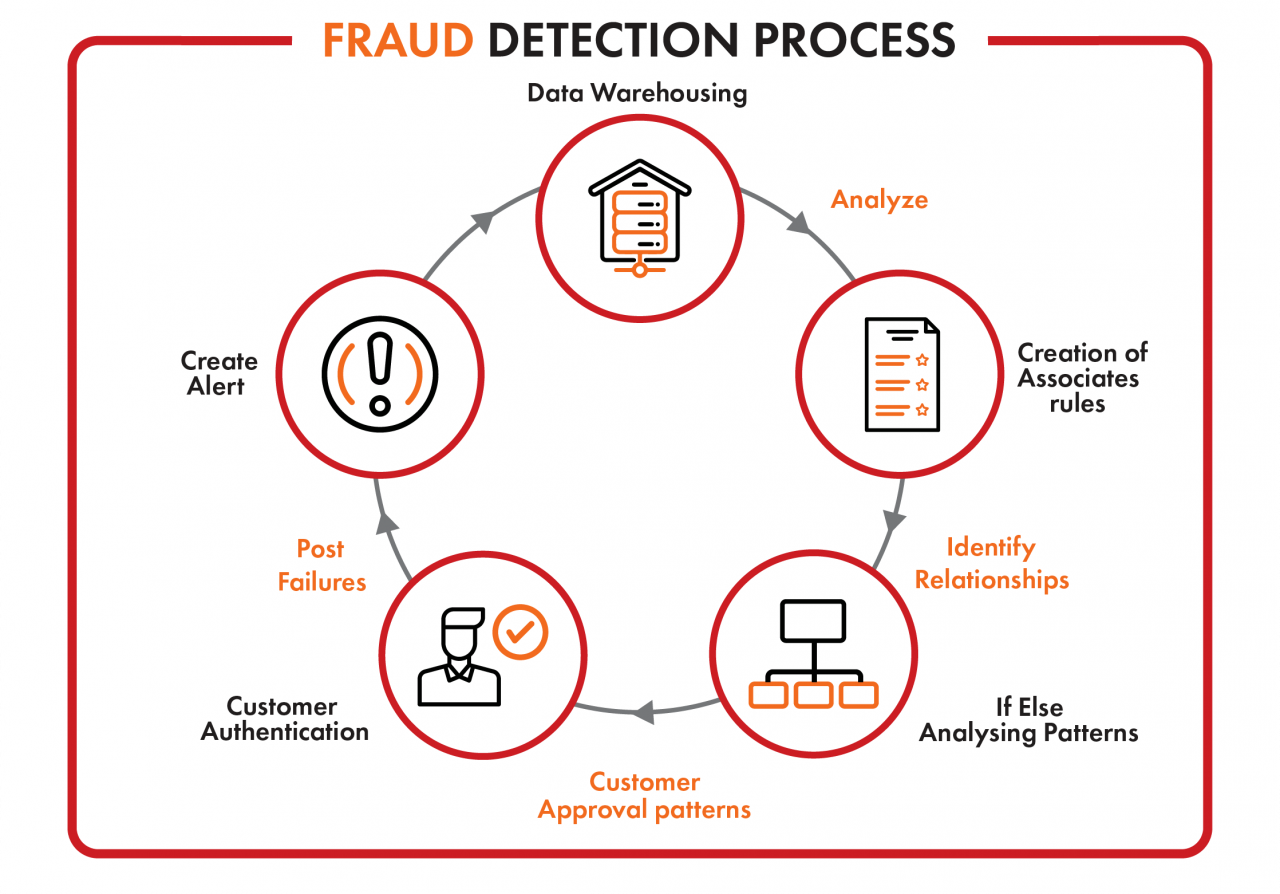
There is no beginning or end to the fraud detection and prevention process. It is a continuous process as each fraud is a learning opportunity and these lessons can be used and incorporated in the improved monitoring and protection procedures of the system. In general the fraud detection and prevention process consists of creating alerts on possible threads, data warehousing and analyzing, identifying rules and detecting patterns, authentication and implementation.
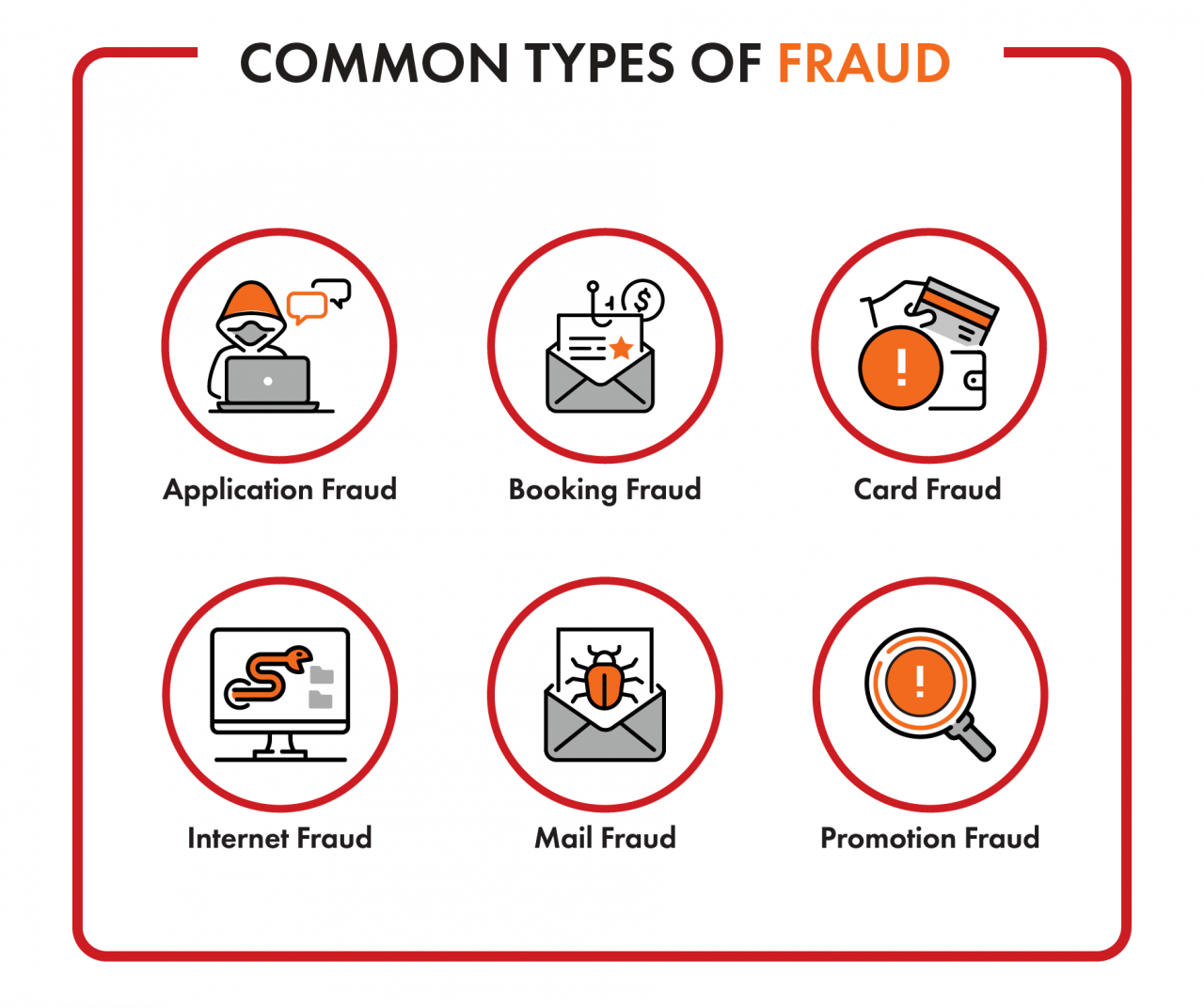
Common Types of Fraud
Although in this case study we’re focusing on fraud detection systems for the telecom industry, it is important to understand that there are many types of fraud which can affect multiple industries. Combating these common types of fraud is pivotal for organizations aiming to fortify their defenses and proactively mitigate the evolving landscape of fraudulent activities.
How We Implemented an Automatic Fraud Alert System for a Telecom Company
Our recent undertaking involved a comprehensive enhancement of a telecom company’s anti-fraud system. Focused on delivering a robust solution, our team responded to the client’s request by implementing fraud whitelisting, multiple threshold configurations, a detailed plan catalog, and enriched alert messaging. Further on we unveil the transformation of the anti-fraud system, detailing the features and improvements that were integrated for heightened security and efficiency.
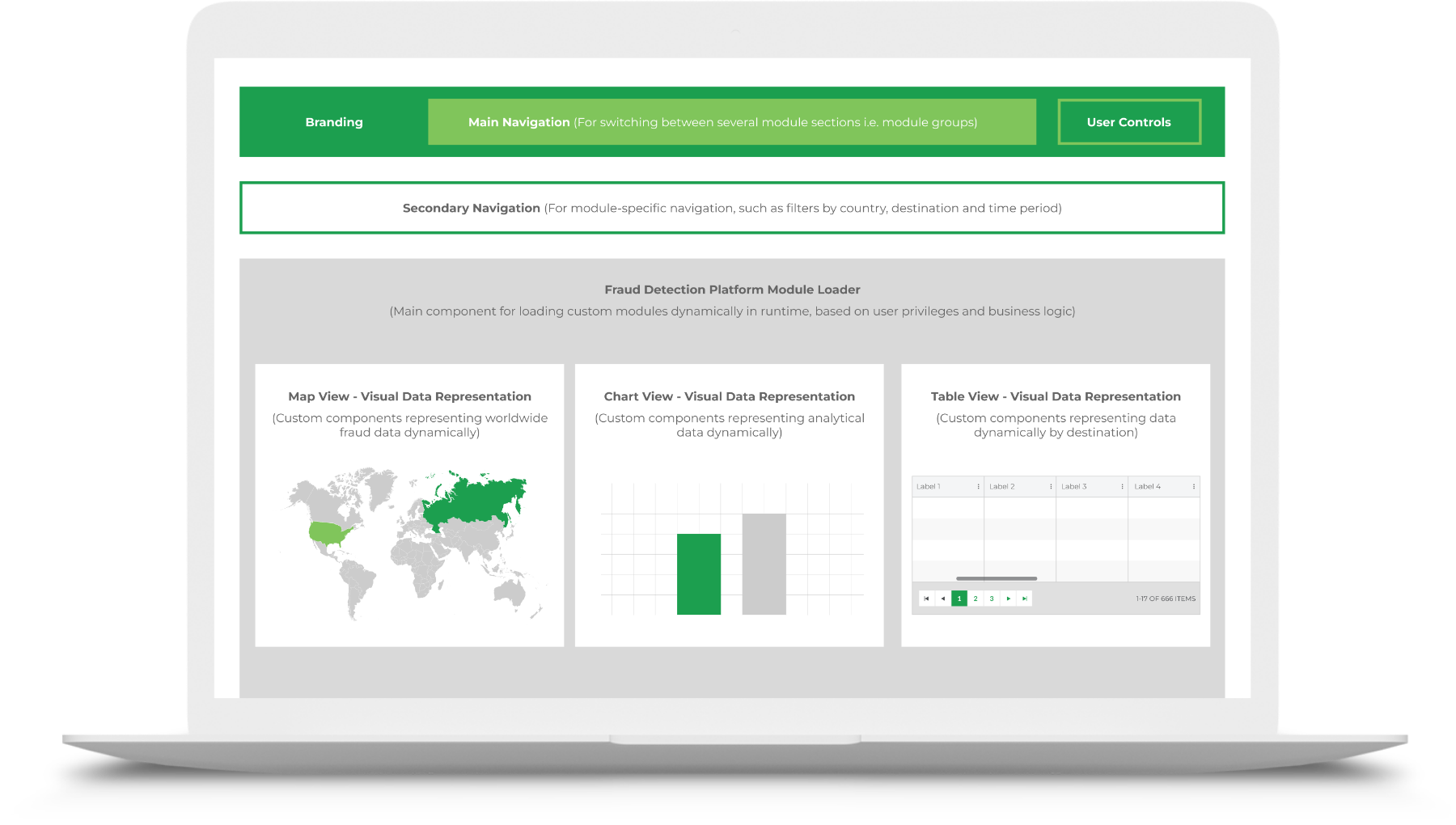
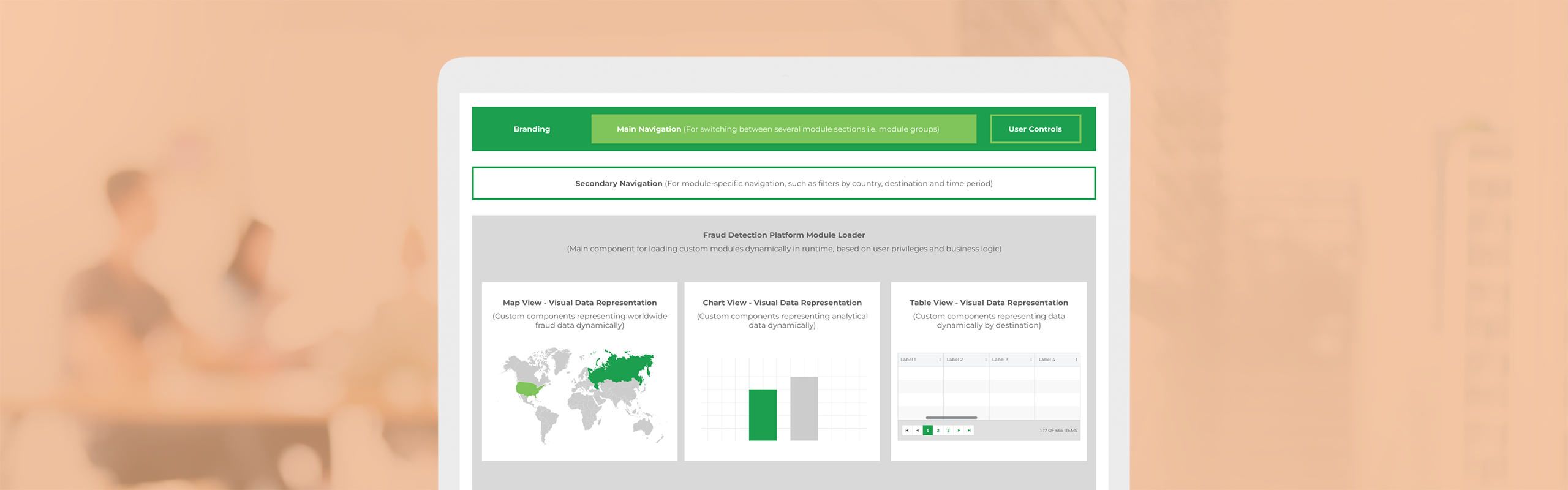
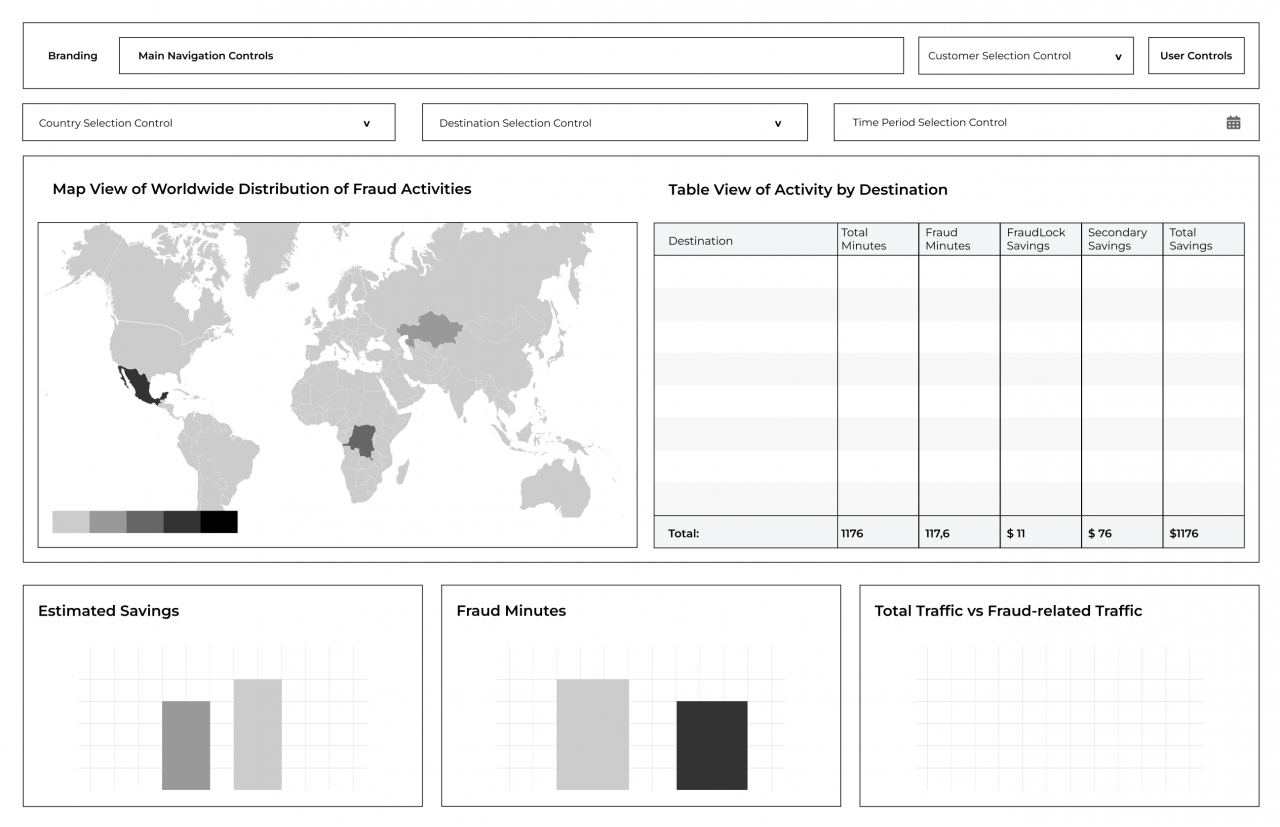
A Comprehensive Fraud Dashboard
Fraudulent activities in the telecom industry pose a significant threat to network security. At Keitaro, we embarked on a mission to fortify telecom security, culminating in the development of a cutting-edge fraud detection system. At the heart of this endeavor lies our Comprehensive Fraud Dashboard, a powerful tool designed to offer unparalleled insights into global fraud activities.
An Interactive Geographic Overview
The map view feature transcends traditional data representation. By visually showcasing the worldwide distribution of fraud activities, telecom operators can identify hotspots, patterns, and emerging trends. This dynamic approach empowers security teams to proactively address threats on a global scale.
Table View for Activity by Destination
Dive into the specifics with a table view, offering a granular breakdown of fraud activities by destination. This detailed analysis equips operators with the knowledge needed to implement targeted security measures, safeguarding specific regions from potential threats.
Chart Views for Strategic Decision-Making
Our chart views are designed to provide actionable insights into critical metrics:
- Estimated Savings: Optimize resources by identifying areas with the most significant potential for savings.
- Fraud Minutes: Gain real-time visibility into fraud-related minutes to minimize impact and enhance network efficiency.
- Total Traffic vs. Fraud-Related Traffic: Compare and contrast network traffic data to pinpoint irregularities and secure telecom operations effectively.
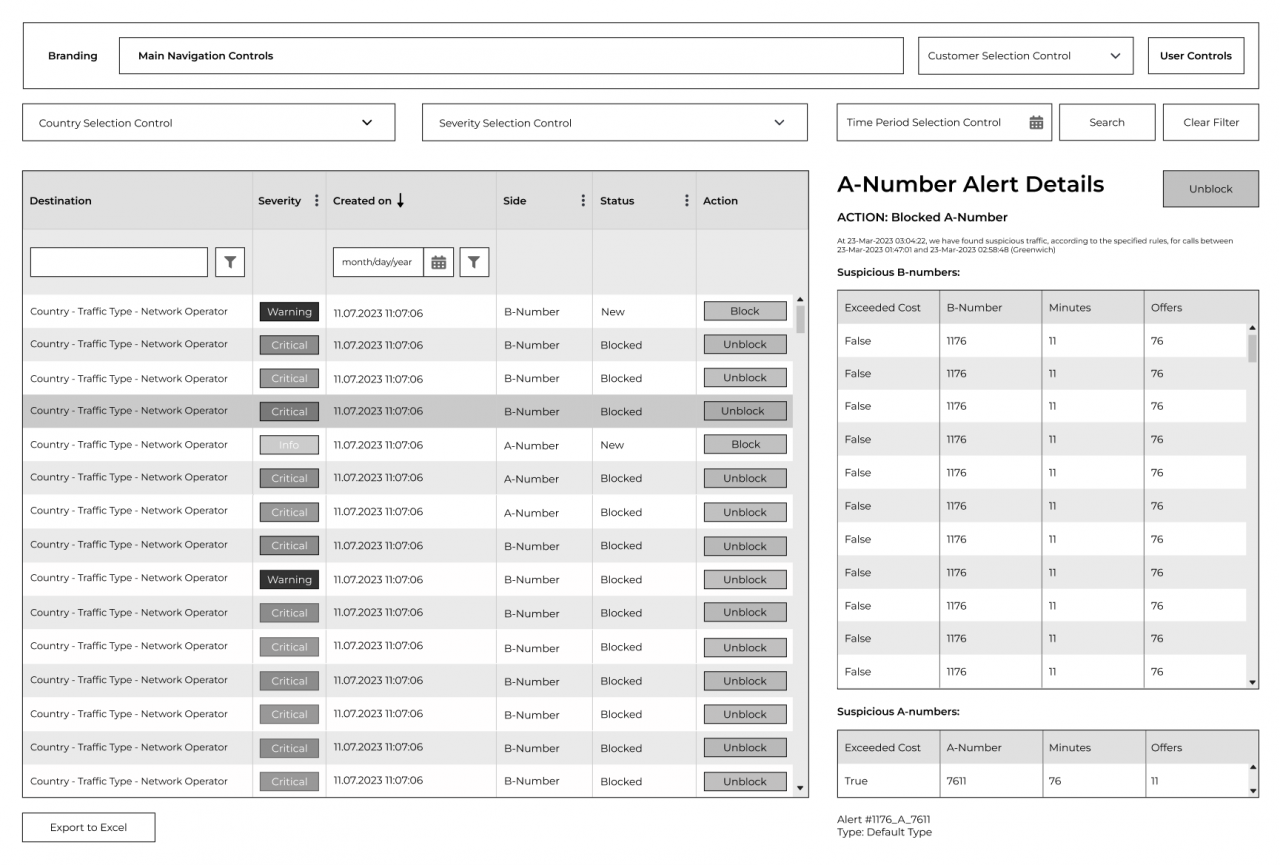
Fraud whitelisting feature
The users of the system are now able to whitelist specific numbers and exclude them from the fraud detection rules that are already in place. The user can also view whitelisted numbers, remove numbers from whitelist and view whitelist history.
Multiple threshold configuration enabled
The severity type configuration file and the database was enhanced to support additional fraud types, the fraud type process was defined and enabled, alert details and mail alerts were enriched to display the fraud types and the threshold configuration editor was extended to support multiple fraud types.
Improved alert detailed messaging
The notifications sent to the users of the system such as alert details, periodic mails and pre-event notifications informing the user of suspicious traffic were improved.
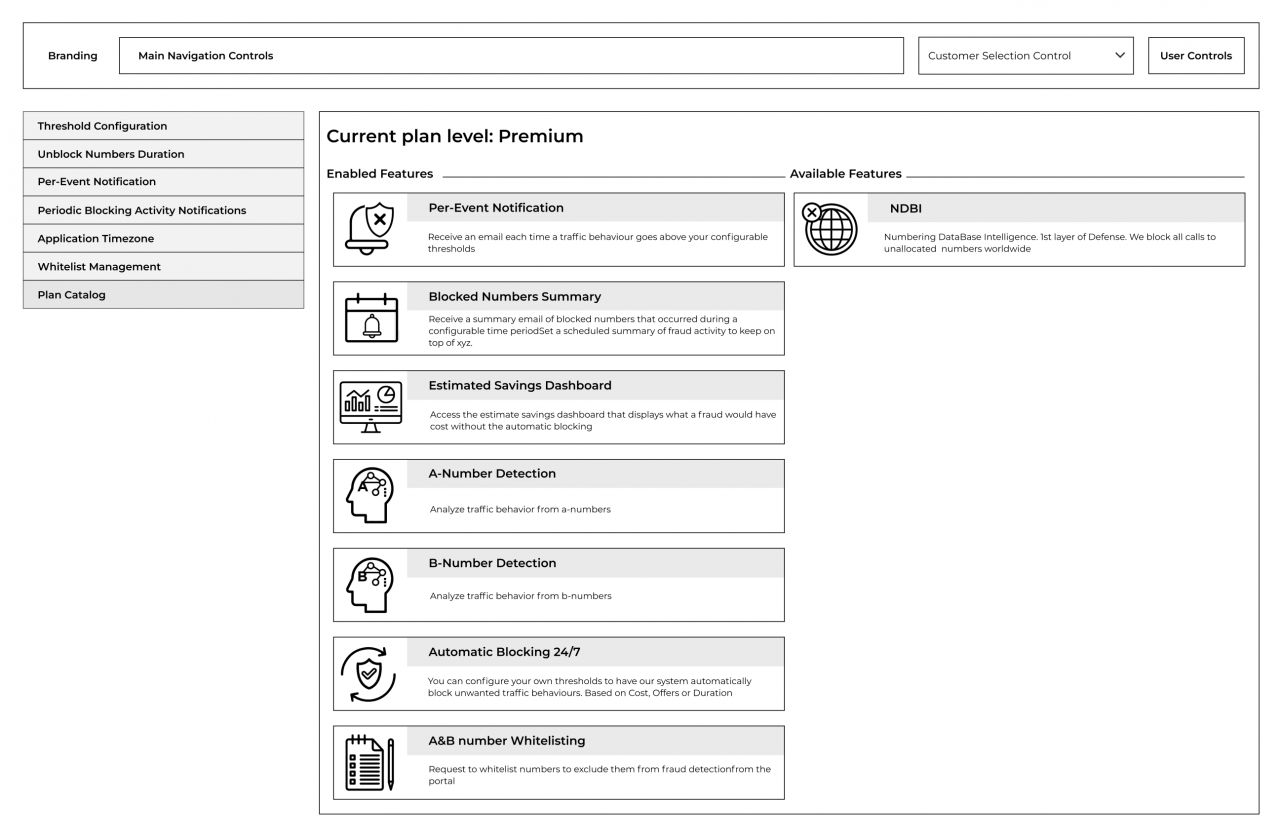
Plan catalog screen
A new screen was implemented where users can see the features that they have and features that the anti-fraud system offers. Management of the available features list was enabled as well as configuration of plans and the features that they cover. Association of features based on the user’s plan as well as mapping features to users on a per-case basis was delivered.
Wrapping Up
So if you have any questions or your organization is in need of a fraud detection and prevention system, feel free to contact us. Our team of highly professional experts can provide you with an automated fraud detection and prevention solution that is a leader in anti-fraud innovation or we can offer you our consultancy to improve and enhance your existing fraud system. Our solution uses real time data and self-learning algorithms for faster detection and implementation of corrective anti-fraud actions.